Cyber Incident Response Form
Cyber Incident Response Form - Abuse or misuse of a system or data in violation of policy. Please provide as much information as you can to answer the following questions to allow cisa to understand your incident. Web cybersecurity (it) incident report template. • a risk rating based on the nccic cyber incident scoring system (nciss). Web an incident response plan template can help organizations outline exact instructions that detect, respond to and limit the effects of security incidents. It is a useful starting point for developing a plan customized to your company's needs. It is intended for internal use only. Web cyber incident reporting this fact sheet explains when to report cyber incidents to the federal government, what and how to report, and types of federal incident response. + more detail do not copy and paste malicious code directly into this form. Web this publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively.
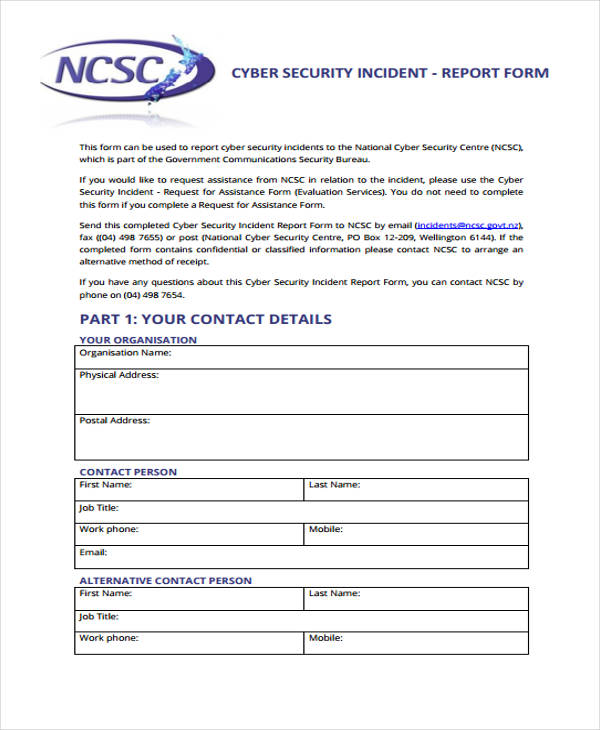
A cybersecurity incident report includes information about a breach and its impact on services or data. Attempts to gain unauthorized access to a system or its data, unwanted disruption or denial of service, or. Web if you would like to report a computer security incident, please complete the following form. Please provide as much information as you can to answer the following questions to allow cisa to understand your incident. Web this publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. When cyber incidents occur, the department of homeland security (dhs) provides assistance to potentially impacted entities, analyzes the potential impact across critical infrastructure, investigates those responsible in conjunction with law enforcement partners, and coordinates the national response to. Provide any mitigation activities undertaken in response to the incident. • a risk rating based on the nccic cyber incident scoring system (nciss). Web cybersecurity (it) incident report template. It is intended for internal use only.
Web this publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. Please provide as much information as you can to answer the following questions to allow cisa to understand your incident. Web if you would like to report a computer security incident, please complete the following form. When cyber incidents occur, the department of homeland security (dhs) provides assistance to potentially impacted entities, analyzes the potential impact across critical infrastructure, investigates those responsible in conjunction with law enforcement partners, and coordinates the national response to. Attempts to gain unauthorized access to a system or its data, unwanted disruption or denial of service, or. It is a useful starting point for developing a plan customized to your company's needs. This revision of the publication, revision 2, updates material throughout the publication to. Abuse or misuse of a system or data in violation of policy. Web cyber incident reporting this fact sheet explains when to report cyber incidents to the federal government, what and how to report, and types of federal incident response. Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs.
Cyber Incident Response Showing Action Plan PowerPoint Templates
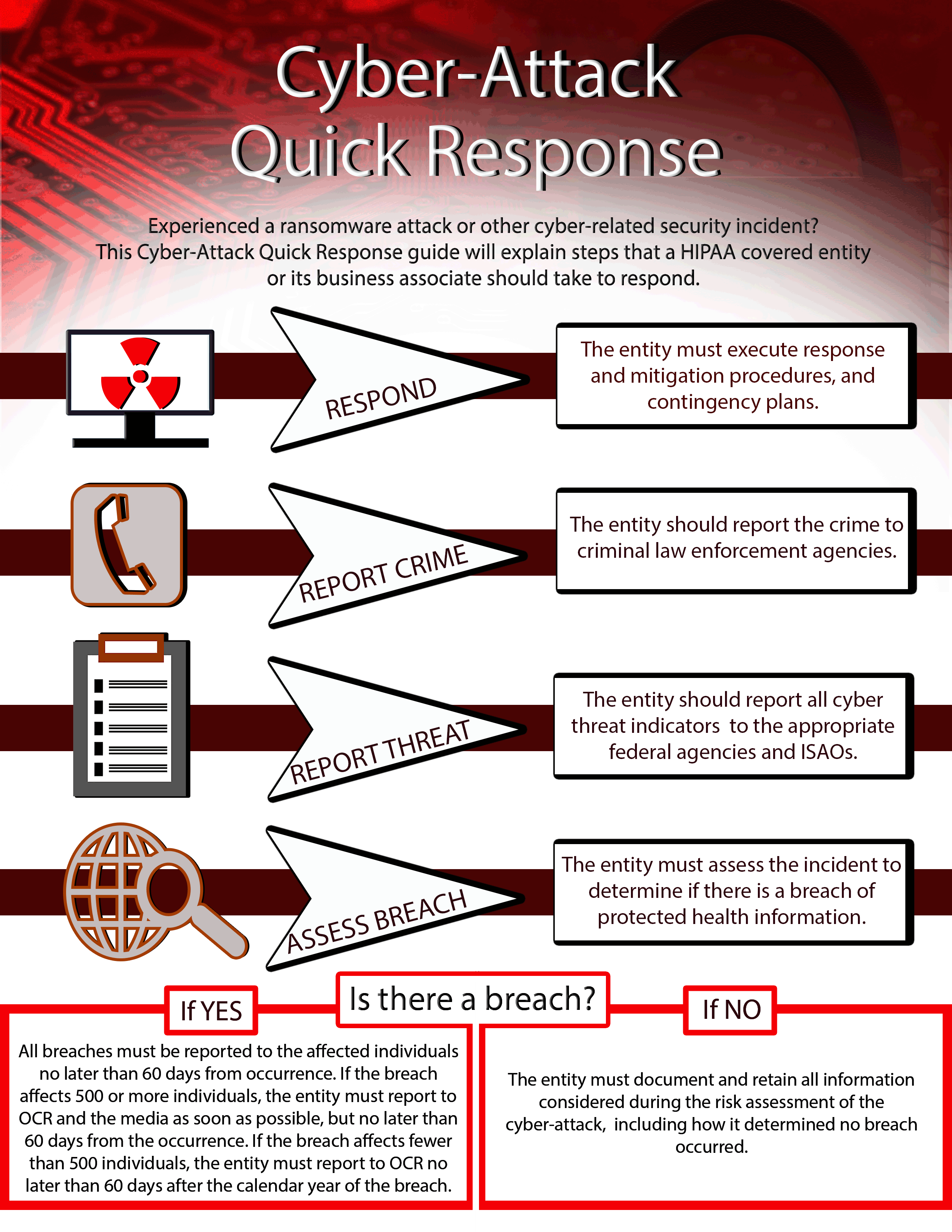
The form assesses how the attacker entered the system and its effect afterward. Provide any mitigation activities undertaken in response to the incident. Web cyber incident reporting this fact sheet explains when to report cyber incidents to the federal government, what and how to report, and types of federal incident response. Web if you would like to report a computer.
Nist Incident Response Plan Template Beautiful Surprising Accountable
• a risk rating based on the nccic cyber incident scoring system (nciss). • a tracking number for the incident. It is intended for internal use only. Web an incident response plan template can help organizations outline exact instructions that detect, respond to and limit the effects of security incidents. Provide any mitigation activities undertaken in response to the incident.
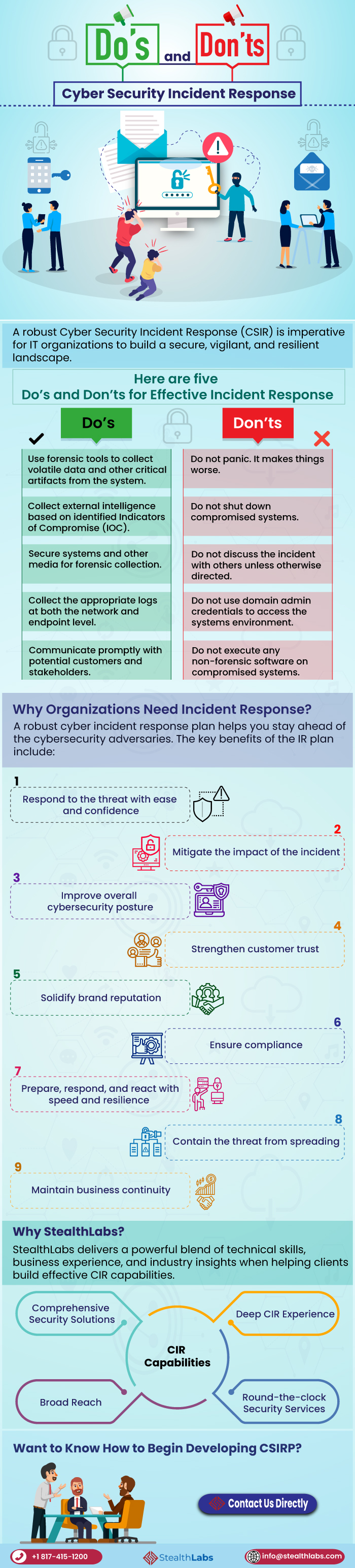
Infographic Do’s and Don’ts of Cyber Security Incident Response
Fill out this incident report in detail. Attempts to gain unauthorized access to a system or its data, unwanted disruption or denial of service, or. It is a useful starting point for developing a plan customized to your company's needs. Abuse or misuse of a system or data in violation of policy. Please provide as much information as you can.
Cyber Security Incident Report Template For Your Needs
Web cyber incident reporting this fact sheet explains when to report cyber incidents to the federal government, what and how to report, and types of federal incident response. When cyber incidents occur, the department of homeland security (dhs) provides assistance to potentially impacted entities, analyzes the potential impact across critical infrastructure, investigates those responsible in conjunction with law enforcement partners,.
Cyber Security Incident Report Template Word Master Template
Provide any mitigation activities undertaken in response to the incident. Please provide as much information as you can to answer the following questions to allow cisa to understand your incident. Attempts to gain unauthorized access to a system or its data, unwanted disruption or denial of service, or. Web cyber incident reporting this fact sheet explains when to report cyber.
Cyber Security Incident Report How to create a Cyber Security
Click to download our free, editable incident response plan template. Attempts to gain unauthorized access to a system or its data, unwanted disruption or denial of service, or. Web an incident response plan template can help organizations outline exact instructions that detect, respond to and limit the effects of security incidents. Please provide as much information as you can to.
Cyber Security Incident Report Template For Your Needs
• a risk rating based on the nccic cyber incident scoring system (nciss). The form assesses how the attacker entered the system and its effect afterward. Web cybersecurity (it) incident report template. Web if you would like to report a computer security incident, please complete the following form. Election offices can use this information as a basic cyber incident response.
Incident Report Form FREE DOWNLOAD Printable Templates Lab
Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs. A cybersecurity incident report includes information about a breach and its impact on services or data. Please provide as much information as you can to answer the following questions to allow cisa to understand your.
Editable Cyber Security Report Template Excel Incident report form
The form assesses how the attacker entered the system and its effect afterward. • a risk rating based on the nccic cyber incident scoring system (nciss). Web if you would like to report a computer security incident, please complete the following form. A cybersecurity incident report includes information about a breach and its impact on services or data. Web november.
Cybersecurity Task Force Issues
Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs. Web this publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. Web cybersecurity (it) incident report template. Attempts to gain unauthorized access to a system or its data,.
Provide Any Mitigation Activities Undertaken In Response To The Incident.
It is intended for internal use only. Click to download our free, editable incident response plan template. Fill out this incident report in detail. Web cyber incident reporting this fact sheet explains when to report cyber incidents to the federal government, what and how to report, and types of federal incident response.
Web If You Would Like To Report A Computer Security Incident, Please Complete The Following Form.
Web cybersecurity (it) incident report template. Attempts to gain unauthorized access to a system or its data, unwanted disruption or denial of service, or. When cyber incidents occur, the department of homeland security (dhs) provides assistance to potentially impacted entities, analyzes the potential impact across critical infrastructure, investigates those responsible in conjunction with law enforcement partners, and coordinates the national response to. Web november 02, 2021 the planning guide and templates are voluntary tools to help jurisdictions effectively recognize and respond to potential cyber incidents.
Abuse Or Misuse Of A System Or Data In Violation Of Policy.
Web an incident response plan template can help organizations outline exact instructions that detect, respond to and limit the effects of security incidents. Election offices can use this information as a basic cyber incident response plan or integrate it into a broader plan based on their specific needs. A cybersecurity incident report includes information about a breach and its impact on services or data. • a tracking number for the incident.
• A Risk Rating Based On The Nccic Cyber Incident Scoring System (Nciss).
Web this publication assists organizations in establishing computer security incident response capabilities and handling incidents efficiently and effectively. This revision of the publication, revision 2, updates material throughout the publication to. + more detail do not copy and paste malicious code directly into this form. Please provide as much information as you can to answer the following questions to allow cisa to understand your incident.