Form Used To Record End Of Day Security Checks
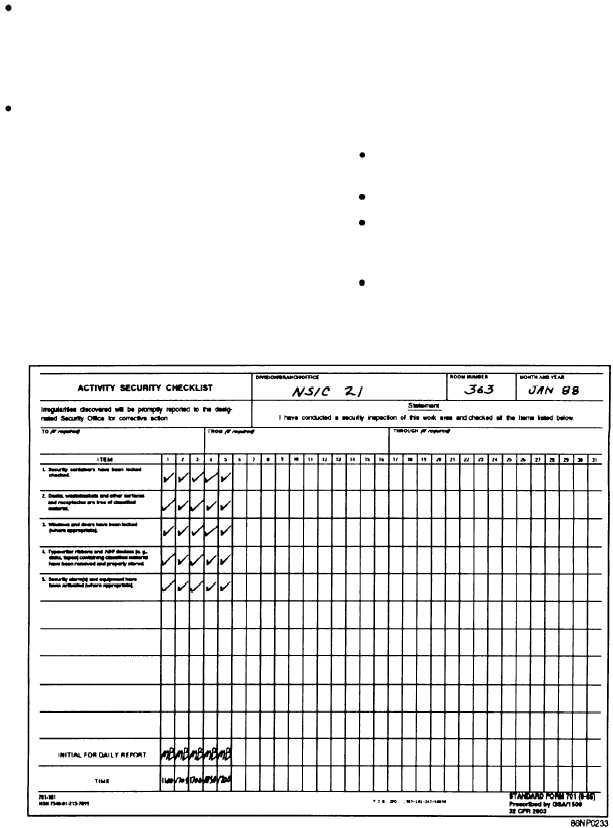
Form Used To Record End Of Day Security Checks - Required for continued secret and confidential clearance eligibility. Web the sf 701, or the activity security checklist, is used to record your end of day checks. Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. The sf 701 shall be retained and disposed of as required by the component records management schedule. Here at the ndc, the sf 701 is kept on record until the next compliance inspection is conducted by higher headquarters. This form is also used to document any incidents that have occurred during the day. Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of the following?, what form is used to. Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds classified. Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place.
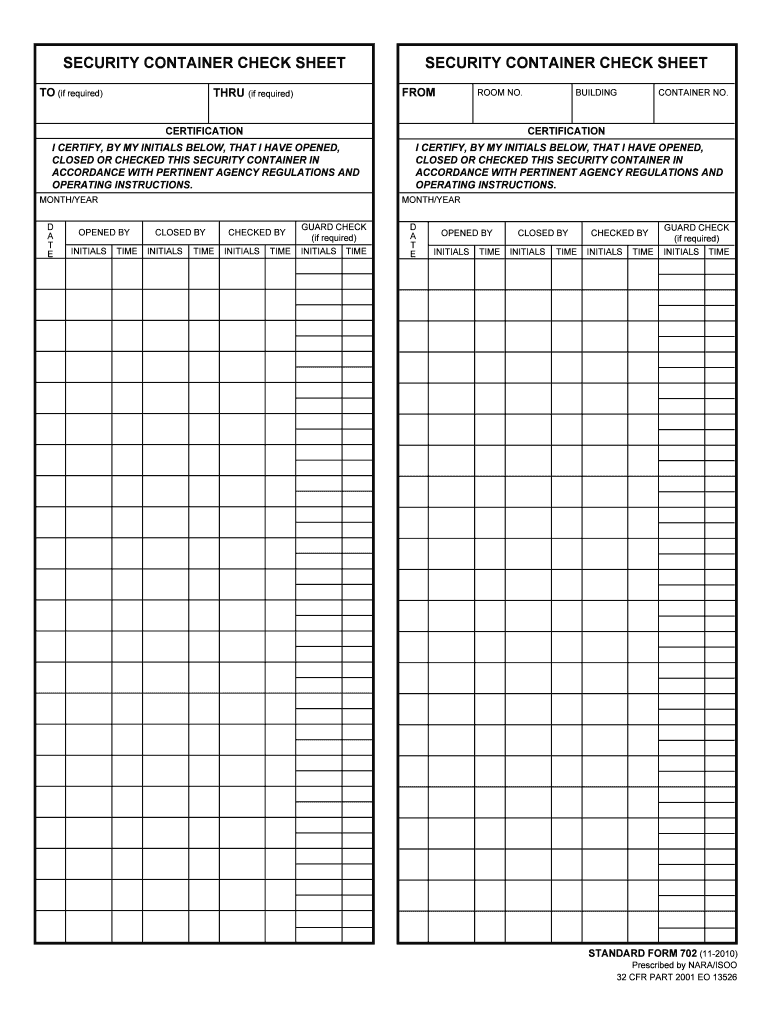
The sf 702, or the security container check sheet, is used to record the opening and closing of your security container. Web the sf 701, or the activity security checklist, is used to record your end of day checks. Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of the following?, what form is used to. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place. This form is also used to document any incidents that have occurred during the day. Required for continued secret and confidential clearance eligibility. Tier 3r periodic reinvestigations will continue to. Web periodic reinvestigation under the fis, there are two types of periodic reinvestigations for national security clearances: Here at the ndc, the sf 701 is kept on record until the next compliance inspection is conducted by higher headquarters.
Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. Required for continued secret and confidential clearance eligibility. Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies. This form is also used to document any incidents that have occurred during the day. Tier 3r periodic reinvestigations will continue to. Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. The sf 702, or the security container check sheet, is used to record the opening and closing of your security container. The sf 701 shall be retained and disposed of as required by the component records management schedule. Web the sf 701, “activity security checklist,” shall be used to record security checks. Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of the following?, what form is used to.
End of day checks Ensure your retail premises are secure
Required for continued secret and confidential clearance eligibility. Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies. Web the sf 701, “activity security checklist,” shall be used to record security checks. The sf 701 shall be retained and disposed of as required by the component records management schedule. Web [narrator:] per.
Security Checklist PDF
Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies. Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of the following?, what form is used to. Here at the ndc, the sf.
Building Security Checklist Template Elegant Free Fire Inspection
Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of the following?, what form is used to. Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies. The sf 702, or the security.
Security Check Report
Web the sf 701, “activity security checklist,” shall be used to record security checks. Here at the ndc, the sf 701 is kept on record until the next compliance inspection is conducted by higher headquarters. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place. Sf 701.
End Of Day Cash Register Report Template charlotte clergy coalition
Records management schedules) to ensure availability for audits and resolution of subsequent discovery of security incidents or discrepancies. Tier 3r periodic reinvestigations will continue to. Web the sf 701, or the activity security checklist, is used to record your end of day checks. The sf 701 shall be retained and disposed of as required by the component records management schedule..
Sf702 PDF SECURITY CONTAINER CHECK SHEET TOif Form Fill Out and Sign
Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds classified. Here at the ndc, the sf 701 is kept on record until the next compliance inspection is conducted by higher headquarters. Records management schedules) to ensure availability for audits.
DesignsnPrint Updates Its High Security Checks with Nine New Features
The sf 702, or the security container check sheet, is used to record the opening and closing of your security container. Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened,.
pdfFiller. Online PDF form Filler, Editor, Type on PDF, Fill, Print
Here at the ndc, the sf 701 is kept on record until the next compliance inspection is conducted by higher headquarters. Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. The sf 701 shall be retained and disposed of as required by the component records management schedule. Tier 3r periodic reinvestigations will.
SECURITY CHECKS 14244_226
Web the standard form (sf) 702 security container check sheet provides a record of the names and times that persons have opened, closed and checked a particular container that holds classified. The sf 701 shall be retained and disposed of as required by the component records management schedule. Web the sf 701, or the activity security checklist, is used to.
SF 701 Instructions Security Checks Matter
Web the sf 701, “activity security checklist,” shall be used to record security checks. Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of.
Records Management Schedules) To Ensure Availability For Audits And Resolution Of Subsequent Discovery Of Security Incidents Or Discrepancies.
Web the sf 701, “activity security checklist,” shall be used to record security checks. Web study with quizlet and memorize flashcards containing terms like what form is used to request a background investigation?, the physical security program prevents unauthorized access to which of the following?, what form is used to. The sf 702, or the security container check sheet, is used to record the opening and closing of your security container. Required for continued secret and confidential clearance eligibility.
Web The Standard Form (Sf) 702 Security Container Check Sheet Provides A Record Of The Names And Times That Persons Have Opened, Closed And Checked A Particular Container That Holds Classified.
Sf 701 the personnel security program establishes ________ for personnel security determinations and overall program management responsibilities. Tier 3r periodic reinvestigations will continue to. Here at the ndc, the sf 701 is kept on record until the next compliance inspection is conducted by higher headquarters. Web the sf 701, or the activity security checklist, is used to record your end of day checks.
The Sf 701 Shall Be Retained And Disposed Of As Required By The Component Records Management Schedule.
Web periodic reinvestigation under the fis, there are two types of periodic reinvestigations for national security clearances: This form is also used to document any incidents that have occurred during the day. Web [narrator:] per enclosure 2, paragraph 9, end of day security checks, the heads of activities that process or store classified information shall establish a system of security checks at the close of each duty and/or business day to ensure that any area where classified information is used or stored is secure. This form is used to ensure that all security measures have been met and that no unauthorized persons or activities have taken place.







.jpg)